In 2007, Certegy Check Services, a subsidiary of Fidelity National Information Services, revealed that one of its employees had been pocketing customer records and selling them to a data broker. Records included credit card, bank account and other personal information, and according to Network World, a weekly IT publication, Certegy estimated the breach affected 8.5 million customers. The thief got jail time, a multimillion-dollar fine, and Certegy paid out nearly $1 million in donations and court costs.
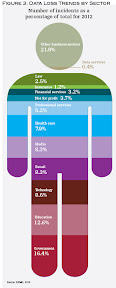
Certegy isn’t alone. Data loss attacks affected more than 1 billion people in the last five years and more than 60 percent of those incidents were the result of hacking, according to the 2013 Data Loss Barometer report from KPMG, which analyzed incidents since 2007 across industries, types of data loss and global regions.
According to the report, data loss threats have risen substantially with the use of mobile devices for business purposes, and personally identifiable information continues to be the top data loss type. Industries such as health care and professional services, which maintain the largest databases of personal information, saw 18.5 million people affected by PC theft, which accounted for one-third of all data loss incidents in those sectors for the first half of 2012.
“Some people may take data because they think they’ll have a competitive advantage over other applicants if they apply to work for a competitor that does the same type of work. They say, ‘Hire me, I can bring over all of these clients and customers,’” said David Strand, a partner at Fisher & Phillips, a law firm representing employers nationally in employment, labor and employee benefits matters. “Some people unwittingly think, ‘I created this stuff when I was working here, it’s rightfully mine.’”
Andrew Sherman, a senior partner at global law firm Jones Day, said some intellectual property thieves use a psychological justification. “They think, ‘I didn’t get a bonus this year, I’m unhappy with where I am in the company, this is my revenge,” he said. “Others are into the sport of hacking. They’ll tap into databases and remove data just to prove that they can. It gives them a rush.”
Depending on the type of data loss, an incident can be a major risk to a company’s revenue and reputation. That is why having a written policy in place is important. A well-communicated policy dictating the use of company systems, devices and the transfer of information make governing data more manageable.
“The policy should note, ‘Regardless of if you’re using our or your own technology, we can install security software on that device and will monitor that device,’” said Lance Spitzner, training director for SANS Securing the Human, an IT/information security awareness training consultancy. “But mentioning this once isn’t enough; it has to be communicated, trained and measured.”
Spitzner’s team offers metric tools designed to give HR and security leaders the ability to track and measure the impact of their security awareness programs and policies (Figures 1 and 2). These metrics measure the human element, specifically people’s behaviors and awareness toward intellectual property theft.


He said these metrics help conduct a root cause analysis for incidents, and in his experience, most HR leaders discover the vast majority of infected systems and leaks are not a technical issue, but a human issue. Employees slip up, and it affects them as well as the company.
“Continually explain the benefits of the policy to employees,” said Jerry Irvine, chief information officer for IT outsourcer Prescient Solutions and a member of the National Cyber Security Task Force. “By having specific tools in place, adhering to policies, especially regarding their personal devices, they are keeping their personally identifiable information from being stolen. Hacking today, or the target of malicious activity, is no longer just corporate data. Identity theft makes money.”
Irvine said companies should invest in data loss prevention applications, mobile device management and mobile information management products, which are preventative and data-centric as opposed to traditional, reactive security measures. These technologies enforce security policies, block employees from installing malicious apps and encrypt data. By controlling and protecting the data and configuration settings for all mobile devices in the network, HR leaders can reduce support costs and business risks. Irvine said the major pitfall is these tools cannot completely segment personal information from professional information. As a result, everything remains commingled.
“There are dual persona capabilities within mobile devices that are being introduced right now which allow you to have your personal life in one portion of the device and your business life in another portion, but those technologies are too young,” said Scott Eason, global vice president of sales for retail and financial services for Verizon Enterprise Solutions’ Financial Services, a security and IT company. “Even when things are compartmentalized, employees need to know that legally, using a device, work or personal, for business reasons, the company has rights to the data that resides on that device.”
According to Verizon’s 2012 “Data Breach Investigations Report,” most of the thefts are carried out by determined adversaries who target intellectual property as a shortcut to attain a strategic, financial, technological or related advantage. While technology that helps eliminate breaches is a start, Eason said HR leaders need to consider this an engagement issue as much as an IT issue.
“Forty-six percent of theft comes from internal threats or agents,” he said. “Eighty-seven percent of theft comes from external agents. That adds up to more than 100 percent, which means that an employee is collaborating with an external actor to do harm to a company, which is a clear sign of disengagement.”
To prevent this, Eason said it’s important to monitor engagement surveys closely and ensure employees only have access to the data they need to perform their job functions and lose all access after leaving the company. As employees move throughout the firm to different functions, HR leaders must ensure they deactivate data sets that are no longer needed. Employees should not have more information than necessary, and those who are emailing too much data from their professional email to a personal account should be monitored.
“With big data trends, analytics and data mining, your information is the premier asset of your company,” Jones Day’s Sherman said. “This is dynamic information that may have multiple revenue streams attached to it. The more training, communicating and engaging you do, the better it is for your business.”















